The facts on the ground are unequivocal – remote work is here to stay. Over the past eight months, enterprises have transitioned employees to work from home, as well as shifting work to less affected regions. These changes, which accelerated trends that began almost a decade ago, have irreversibly transformed the way companies work. Shopify, for example, has closed its offices until later in 2021 and is re-designing operations for the “new normal” where most employees work remotely.
Previously treated from an IT standpoint as second-class citizens, today’s remote workers demand the same performance and user experience they had at corporate headquarters. To ensure business as usual in this new flat world, enterprises need remote working solutions that enable fast and secure productivity from any location and device.
Zero Trust Is More Important Now Than Ever
The fundamental shift in the way enterprises work has forced them to rethink their data protection strategies. Users are spread across dozens and hundreds of branch offices, while workloads move across multiple data centers and clouds. At the same time, work-from-home and Bring Your Own Device (BYOD) are more widespread than ever. These trends have combined to enlarge enterprises’ attack surface.
Security and IT teams understand that user identities can be compromised, and that the communication source is now meaningless from a security standpoint. Even the LAN – once the bastion of corporate security – can no longer be automatically trusted.
This realization has accelerated the adoption of a “zero trust” approach based on a very simple principle: Never Trust, Always Verify. Instead of assuming that internal traffic can be trusted, enterprises must verify any device or user trying to connect to their systems before granting access.
In zero-trust architectures, every access attempt is considered “suspicious” until proven otherwise. Systems should never rely on the communication source and should authenticate each access attempt from every endpoint, including devices on the LAN or VPN.
Giving Endpoint Devices the Respect They Deserve
CTERA is the only global file system provider with a Zero Trust architecture. Unlike other solutions, we built our platform with a “security first” approach. We understood from day one that no edge devices (filers, desktops, laptops) should be trusted when it comes to branch offices or WFH users.
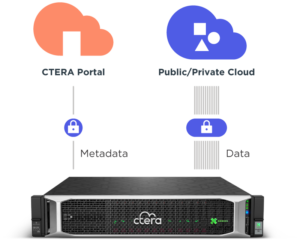
CTERA edge filers communicate only with the core servers and are never granted credentials to access object storage.
In addition to the clear security benefits of a zero-trust architecture, this approach also gives enterprises a unique advantage with respect to remote workers. CTERA’s architecture allows desktop, laptop and mobile clients (CTERA Drive) to access the global file system directly without going through the edge filer, enhancing both performance and scalability.
Focusing initially on highly privileged, trusted cloud storage gateways, our competitors didn’t have this integrated capability for remote endpoints. Faced with the challenge of enabling work-from-home, these vendors were forced to bolt on a clunky solution using a filer to mediate between endpoint clients and the global file system. This additional level of redirection increases latency, drives up maintenance costs and hampers scalability.
By implementing a zero-trust architecture from day one, CTERA’s global file system treats endpoint devices as first-class citizens of the global filesystem. All users are treated equally – whether they’re working in the branch office or accessing a file from home. That’s why CTERA is the only solution proven to support tens of thousands of concurrently active endpoint devices. By leveraging this inclusive approach, one of our customers was able to transition its entire workforce of 100,000 employees to work from home – within a single day.
The World Is Your Office
Want to learn more about how CTERA’s Zero Trust architecture can help your organization secure global file access for remote workers? Download our whitepaper. Or drop us a line – we’d be glad to chat.

