Defining Ransomware in the Cloud
Ransomware in the cloud refers to ransomware attacks that target organizations’ cloud-based resources. Such attacks seek to compromise cloud services, applications, and storage systems, including servers, databases, file storage, and others.
If attackers are successful, they can render cloud-based resources inaccessible, potentially causing major interruption or even shutting an organization down until the situation is resolved. The consequences of a successful attack can be devastating, with financial, legal, and reputational consequences.
This couldn’t be more relevant, as highly damaging ransomware attacks against the public sector show no sign of abating. Recently, Key Biscayne became the third local Florida government to get hit by ransomware within one month. This incident came on the heels of two widely publicized attacks that shut down email servers, emergency response systems and online public services in Lake City and Riviera Beach, Florida.
Highly damaging ransomware attacks against the public sector show no sign of abating. A couple of weeks ago, Key Biscayne became the third local Florida government to get hit by ransomware within one month. This incident came on the heels of two widely publicized attacks that shut down email servers, emergency response systems and online public services in Lake City and Riviera Beach, Florida.
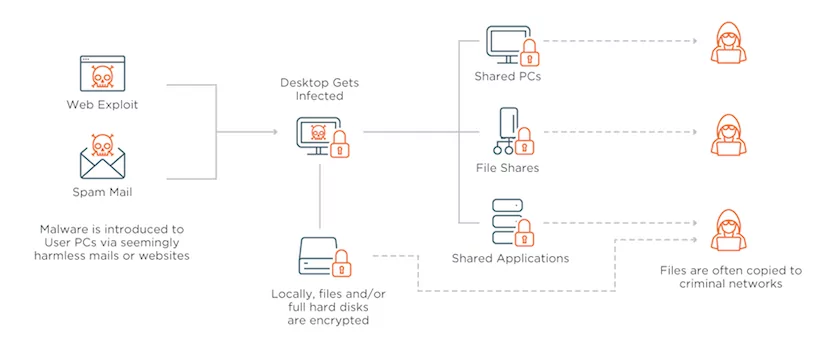
How Ransomware in the Cloud Works
Ransomware locks down an organization’s IT systems and demands a ransom payment (typically in Bitcoin) in return for a decryption key. In the cases of Lake City and Riviera Beach, the victims paid a total of more than $1 million to decrypt their data and regain access to their systems.
In all three instances, the attack started when city employees unknowingly clicked on an email attachment (i.e., phishing) that infected their computers with malware. Once installed on an endpoint device, today’s sophisticated ransomware can quickly spread across the network and lock down an entire organization.
Why Organizations are Vulnerable to Cloud Ransomware
Ransomware attacks are difficult to stop because they target the weakest leak in the IT security chain – the user. These attacks are particularly common in public sector organizations, like municipalities and hospitals, which typically have antiquated IT systems and lack advanced security tools and user training.
Equally disturbing is the fact that many ransomware victims simply choose to pay their attackers. This is because the cost of not paying the ransom – permanent loss of critical/sensitive data as well as mitigation and recovery efforts – is exorbitant. The city of Baltimore was hit by ransomware in May 2019 and chose not to pay the hacker’s original demands of $76,000. To their chagrin, recovery efforts took over one month and cost more than $18 million.
How to Protect Against Cloud Ransomware
While you can’t prevent your organization from being targeted by a ransomware attack, you can take steps to protect your data. In this way, you’ll be positioned to avoid paying the ransom and to recover quickly in the event of an attack.
Based on the Department of Homeland Security (DHS) recommendations and other best practices, organizations should take the following measures to protect against ransomware:
- Secure your perimeter and your edge devices (PCs, laptops, etc.)
- Update your systems to include the latest patches and software updates.
- Offer cybersecurity awareness training to your employees and educate users to identify and avoid phishing attacks
- Use antivirus software, firewalls, email filters and other preventative software to guard against malicious network traffic
- Make sure all your data is backed up in a secure and reliable fashion
- Back up all files and systems and retain backup versions in a read-only repository
- Be sure to physically separate your backups from the main copy of your data
Drawbacks of Traditional Ransomware Solutions
While virtually all enterprises and large organizations employ backup products, most of these tools were not built to protect data against ransomware attacks that can lock down a network in minutes. This is because even the most efficient endpoint and server backup products operate with a backup interval setting of 4-8 hours – nearly a full business day.
Thus, in the best-case scenario, this means losing up to a day’s worth of productivity following an attack. If you’ve got hundreds or thousands of users, this is a huge productivity loss.
Effectively fighting back against ransomware requires a data management strategy that goes beyond endpoint security or backup. True data ransomware protection means reducing backup intervals from hours to minutes, while ensuring that data is always encrypted so that it cannot be used by attackers.
Advantages of a Secure Edge-to-Cloud Strategy
End-to-end security is a “must” for protecting data from ransomware and other cyber threats. In modern cloud-driven enterprise environments, this means protecting your data at the edge (where it’s created), in transit (over the network), and in the cloud (where it’s stored).
Building a secure edge to cloud strategy can help organizations protect their data and prevent potential damage from ransomware and other cyber threats. Such a data management strategy should include the following key elements:
- Virtual Private Cloud – Data management and file services should be performed 100% within the firewall – whether on-premises or using public cloud infrastructure.
- End-to-End Encryption – Source-based encryption should be used to secure data before it leaves your devices, offices and servers. This means that in the event of an attack, even if your data is temporarily locked, it cannot be read.
- Smart Data Control/Protection – Global File Systems let you track file changes across the entire organization and create incremental versions of files as they are updated, reducing recovery point exposure from hours to minutes.
With such a strategy in place, data can be restored in minutes and operations can resume as usual. You’re in control of your data, and you’re no longer vulnerable to the hacker’s demands.
As the attack landscape continues to evolve, I believe we’ll see more and more enterprises and large organizations adopting secure edge-to-cloud solutions to meet their growing data protection and business needs and prevent ransomware.
FAQs
- Can ransomware affect cloud storage?
Yes, ransomware can affect cloud storage in the same way that it affects local storage.
- What are the risks associated with ransomware attacks on the cloud?
Risks of ransomware in the cloud include denial of access to key resources, business interruption, financial consequences, legal and regulatory consequences, data theft, loss of customers, and long-term reputational damage.
- How do large organizations protect against ransomware attacks?
Large organizations often implement a multi-layered approach to protect against ransomware attacks, including:
- Security Awareness Training: Educating employees about phishing and safe online practices to reduce the likelihood of infection
- Regular Backups: Creating and maintaining frequent backups of critical data to ensure recovery without paying ransom
- Endpoint Security: Deploying advanced antivirus and anti-malware solutions to detect and block ransomware at endpoints
- Network Segmentation: Segmenting networks to limit the spread of ransomware and isolating infected systems
- Patch Management: Keeping software, operating systems, and applications up to date with the latest security patches
- Email Filtering: Using email filtering solutions to detect and block phishing emails containing ransomware
- Intrusion Detection Systems (IDS): Implementing IDS to monitor network traffic and detect unusual or malicious activities
- User Access Control: Enforcing the principle of least privilege to restrict unnecessary access to critical systems and data
- Multi-Factor Authentication (MFA): Requiring additional verification beyond passwords for accessing sensitive accounts and systems
- Incident Response Plan: Developing a comprehensive plan to respond to and recover from ransomware incidents effectively
- Security Audits: Conducting regular security assessments and audits to identify vulnerabilities and weaknesses
- Vendor Security: Ensuring that third-party cloud service providers have robust security measures in place
Related Resources:
- Ransomware Mitigation: The Ins And Outs Of Modern Attacks
- How to Protect your Backups from Ransomware
- What is Ransomware?