CTERA Ransom Protect
Defend Your Data with
AI-Powered Ransomware Protection
Deploy Advanced AI Defense
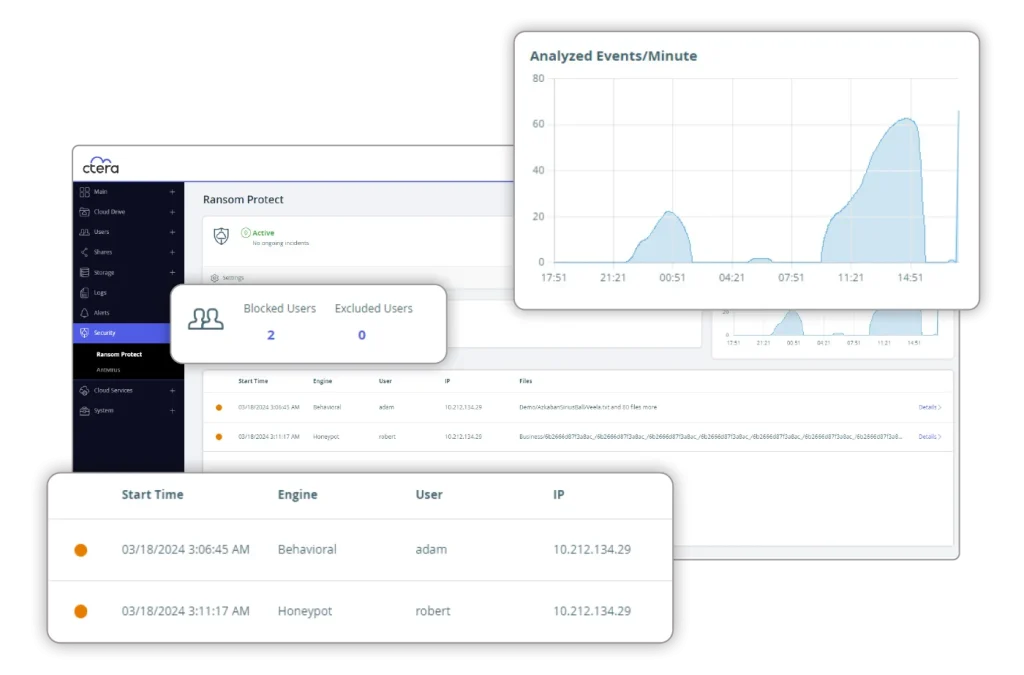
CTERA Ransom Protect uses sophisticated machine learning algorithms to identify and block suspicious file activities quickly.
Administrators can monitor attacks in real time via an incident management dashboard, which also stores extensive incident evidence and logs for post-attack forensics. Integrated into the CTERA Edge Filer, Ransom Protect is easily activated with a single click for streamlined deployment.
Close the Backup Gap
Traditional backup systems are inadequate for fast-moving ransomware attacks, often backing up data only every 8 to 24 hours, leading to unacceptable data loss. CTERA offers continuous real-time protection, synchronizing data to air-gapped, immutable object storage. This ensures superior ransomware protection with a recovery point objective (RPO) measured in minutes or seconds.
Achieve Instant Disaster Recovery
CTERA’s caching technology continuously replicates data to the cloud, providing near-immediate disaster recovery and ransomware mitigation, even for terabytes of data. When rolling back a folder to a previous version in the cloud, the Edge Filer instantly populates with stubs, allowing users to quickly regain access to recovered files on their mapped network drives without waiting for all data to be restored.
Safeguard Data with Immutable Snapshots
Over 90% of ransomware attacks target backups. CTERA combats this by securely storing snapshots in immutable, air-gapped object storage, which cannot be deleted or modified during the retention period. This strategy creates a safe haven for your data, preventing ransomware from destroying your recovery options.
Enhance Security with Zero-Trust Architecture
CTERA is the only global file system with Zero-Trust architecture. Edge Filers never store or receive credentials for object storage. All storage operations are performed with single-use tokens provided by an authorization service in the CTERA Portal, ensuring maximum security.

Trust in Our Data Exfiltration Prevention
CTERA’s Ransom Protect Honeypot capability uniquely deploys decoy files within your organization’s file system to detect and stop unauthorized access or data theft, neutralizing threats before they cause significant damage.
Resources
Solution Sheets: CTERA Ransomware Protection Solution Sheet
Fighting back against ransomware requires a risk management strategy that goes beyond data security or backup products. While you can’t prevent your organization from being targeted by a ransomware attack, you can take steps to…
Case Studies: Construction Firm Recovers from Ransomware with CTERA and EarthBend
Uncategorized: Ransom Protect Now Features Data Exfiltration Prevention
Last year, the cyber-threat landscape witnessed a disturbing escalation in ransomware attacks, with cybercriminals employing double extortion tactics that coupled encryption with the insidious threat of data exfiltration. At CTERA, we comprehend the severe ramifications of such attacks, where sensitive data, including personal and confidential information, is not only held hostage but also potentially leaked…
Videos: Storage Field Day 26 – How CTERA Uses AI to Solve Ransomware Challenges
Ransomware protection is moving from a defensive posture utilizing legacy backup methods to an offensive approach utilizing Artificial Intelligence and Machine Learning to thwart attacks before they infiltrate networks. CTERA’s CTO Aron Brand and Saimon…
FAQ
How are ransomware attacks detected?
Our ransomware protection—CTERA Ransom Protect—uses activity sensors integrated into the file system that continuously monitor file-sharing traffic (specifically SMB). This data is processed through advanced machine learning algorithms trained on extensive ransomware attack datasets. The system identifies and responds to behavioral anomalies—such as unauthorized encryption or file manipulation—within seconds, blocking affected users and stopping the attack before damage can spread.
How long would it take if my organization were attacked by ransomware and I needed to recover large quantity of data?
Our instant recovery feature utilizes air-gapped, immutable cloud snapshots, allowing you to immediately access previous versions of affected files. You can initiate the rollback process via your network drives without waiting for a full restoration. This minimizes downtime and ensures near-instant recovery, even for large datasets
Does CTERA rely on signature updates for blocking ransomware?
No, we use Zero-Day protection that doesn’t rely on traditional signature update services. It uses advanced AI and machine learning algorithms to detect and block ransomware attacks. In addition to behavioral anomaly detection, we also offer signature-based malware protection that blocks known attacks.
Enhance Your Security Posture & Ensure Business Continuity
Activate your data defense strategy today. Talk to our team.
