Ransomware Protection & Mitigation with a Global File System
"If it weren't for CTERA, ransomware would have been a devastating and potentially business-closing catastrophe."
- Rob Svendsen, S.J. Louis Construction


Take Back Your Data with AI Ransomware Protection
Fighting back against ransomware requires a risk management strategy that goes beyond data security or backup products. While you can’t prevent your organization from being targeted by a ransomware attack, you can take steps to safeguard your data with ransomware protection.
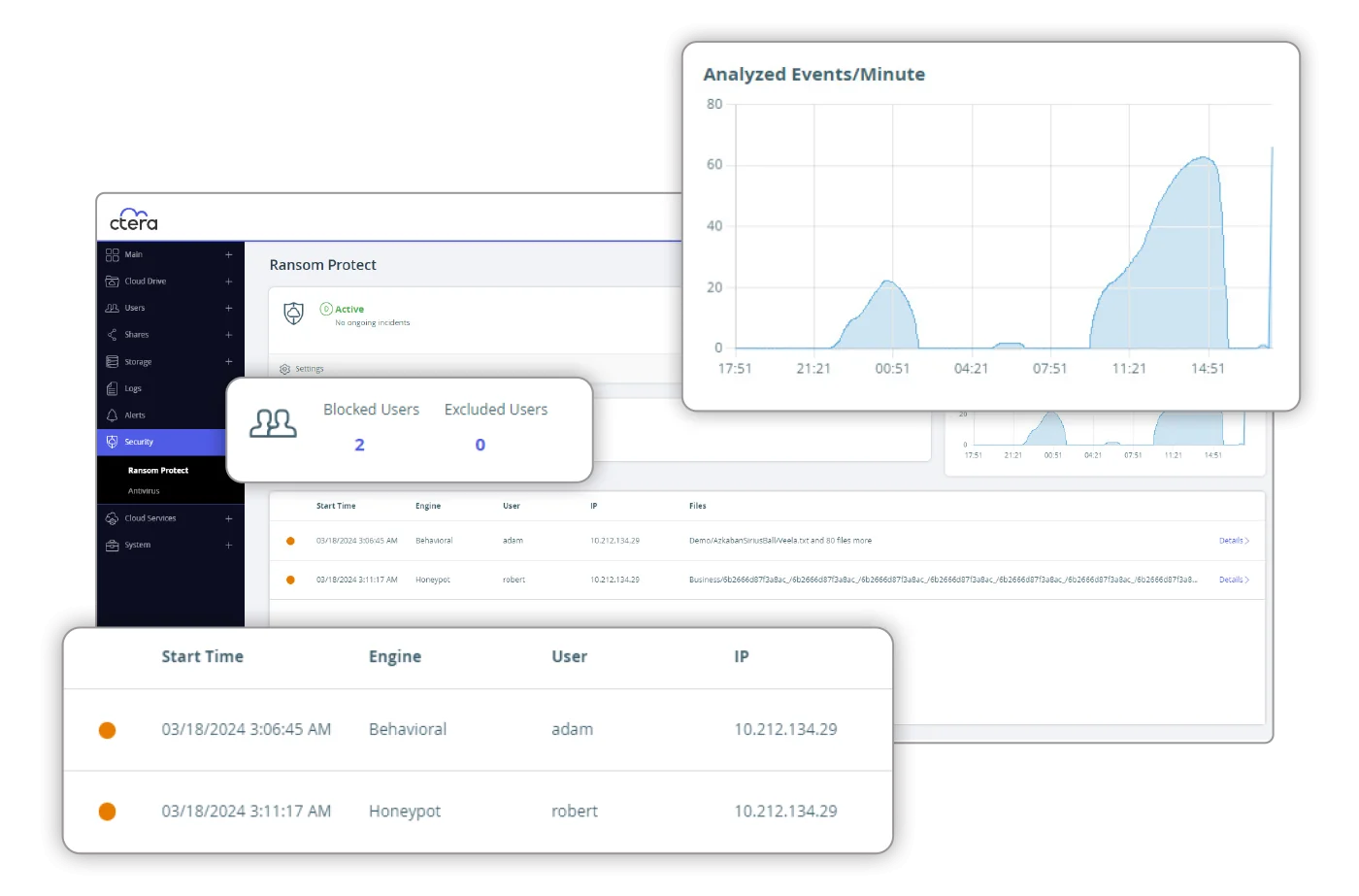
CTERA’s global file system features Ransom Protect, a state-of-the-art AI ransomware protection mechanism that identifies and halts ransomware attacks in real time. Furthermore, should a ransomware attack occur, organizations have the ability to instantly recover the ‘locked’ data from immutable snapshots.
Frequently Asked Questions
-
How are ransomware attacks detected?
CTERA Ransom Protect uses activity sensors integrated into the file system, which feed data into an advanced machine learning algorithm. This algorithm is trained on a large dataset of attack flows and can identify behavioral anomalies that suggest fraudulent file activity. It can block offending users within seconds of detecting an issue.
-
How long would it take if my organization were attacked by ransomware and I needed to recover large quantity of data?
Thanks to CTERA’s advanced caching technology and instant recovery feature, rolling back data following from a ransomware attack can be near-instantaneous. When rolling back a folder to a previous version in the cloud, users immediately regain access to recovered files on their mapped network drives. There is no need to wait for all the damaged data to be restored.
-
Does CTERA rely on signature updates for blocking ransomware?
No, CTERA Ransom Protect offers Zero-Day Protection and does not rely on traditional signature update services. It uses advanced AI and machine learning algorithms to detect and block ransomware attacks. In addition to behavioral anomaly detection, CTERA also offers signature-based malware protection that blocks known attacks.
-
What kind of management tools does CTERA Ransom Protect provide for dealing with ransomware attacks?
CTERA Ransom Protect provides an administrator dashboard that enables real-time attack monitoring, comprehensive incident evidence logging, and post-attack forensics. This helps administrators manage and mitigate incidents more effectively.
-
How are my backups protected against ransomware?
To counter the fact that over 90% of ransomware attacks target backups, CTERA securely stores snapshots in immutable, air-gapped object storage. These cannot be deleted or modified during the retention period, effectively creating a safe haven for your data. This strategy prevents ransomware from destroying your recovery options.
-
Do I need to install additional software to enable the ransomware protection capabilities?
CTERA Ransom Protect can be activated with a single click on CTERA Edge Filers with the latest version release, making it a straightforward and simple solution to deploy. Everything is built in.
-
I already have an EDR (Endpoint Detection and Response) solution, do I still need Ransom Protect?
Yes, even with an EDR (Endpoint Detection and Response) solution, CTERA Ransom Protect is still beneficial due to its layered security approach. EDR may not cover many types of devices, such as printers or medical devices on your network. Remember, it only takes one compromised device to disrupt an entire network. CTERA Ransom Protect adds an extra layer of security, safeguarding your file storage and backup systems, the primary targets of attackers, thus complementing your existing EDR solution and enhancing your defense against ransomware.
AI-Based Ransomware Protection. Back-Up Everything. Roll Back with Sync.