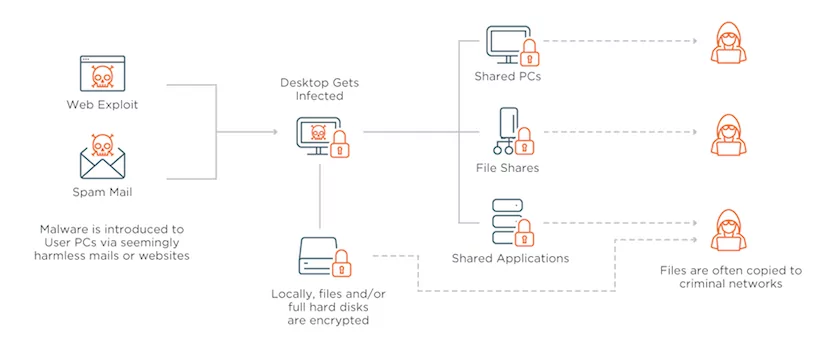
Full disclosure: coming from the high-performance computing industry, the topic of enterprise security is a relatively foreign concept to me. I’ve worked extensively with the world’s largest defense departments in my past lives – but ‘security’ was most commonly used to describe topics such as ‘national security’ and ‘nuclear nonproliferation’. Fast forward to my time at CTERA and I find myself struggling to come to terms with some of the crazy things that IT organizations, large and small, are being subjected to every day.
Enter ransomware. Shedding this discussion of all hyperbole or marketing-speak, I can only say that this form of malware has reached the heights of a global IT epidemic that every organization has either already faced (about 50% of organizations have been breached) or will almost certainly face as the pace of cyber-attacks increases on a daily basis. Here’s what you need to know:
How does ransomware work?
Those are the basics. Two especially nasty tweaks to ransomware that really piss me off:
- Certain cyber-criminals are capturing data that ransomware can copy out of your network for the purposes of selling it to interested third parties, ie: industrial espionage
- There have been reports of cases where customers have paid ransomware attackers and then never receive encryption keys for decrypting their PCs in return
How big is the ransomware epidemic?
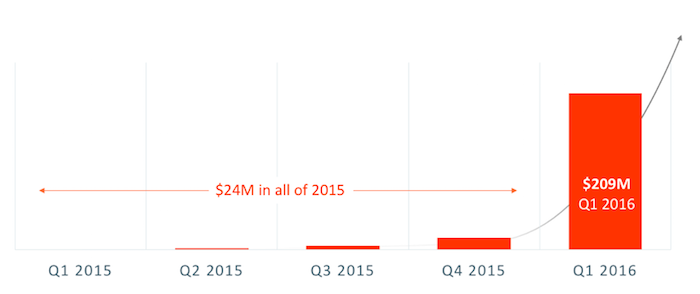
Ransomware payments are made via anonymous bitcoin transactions – where it can cost anywhere from $500-$2,000 to unlock an average PC. Because of the anonymity, it’s difficult to know precisely how many anonymous payments have been paid to cyber-criminals, but there are some recent data points that have emerged to support the claim that this situation is, indeed, a global epidemic.
- In ALL of 2015, the FBI estimates that the world paid $24M USD in ransomware payments
- In just the 1st quarter of 2016, victims paid as much as $209M USD to cyber-criminals
There’s lots of numbers here… I’ll plot this onto a chart for all y’all visual learners:
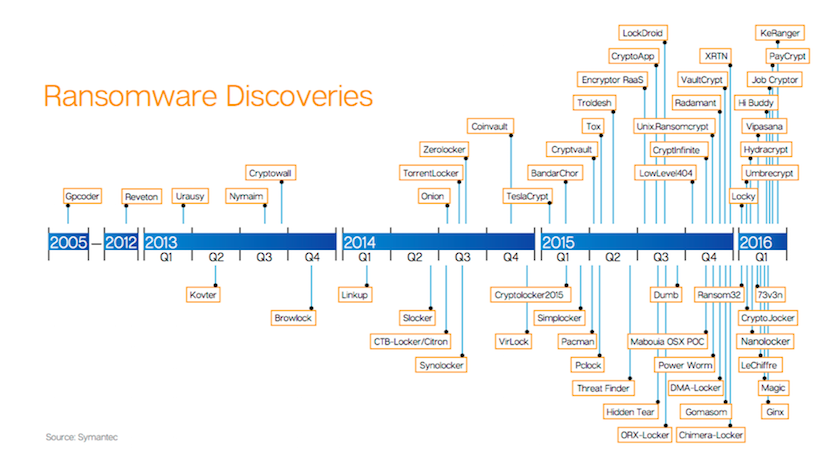
What you see here is an exponential spike in activity. If the numbers are true, ransomware is on track to be a $1B business this year. What’s worse is that we don’t yet know how big this will be because each public ransomware payment is only encouraging cyber-attackers to introduce new strains of malware and redouble their efforts. This graphic from Symantec shows the pace of ransomware innovation and how this can be challenging for IT security companies to keep up:
Source: Symantec Internet Security Threat Report, April 2016
Taking this discussion from the general to the very specific, there are now some very real examples of ransomware attacks in the CTERA customer community:
- As of this month, nearly 50% of CTERA customers surveyed indicate that they’ve been a victim of a ransomware attack
- We now have a number of case studies that we can publicly discuss, thanks to CTERA customers who feel they must come forward and educate the market about the severity of ransomware attacks and how to apply appropriate countermeasures. Here’s two:
[one_fourth] S.J. Louis Construction case study here [/one_fourth] [three_fourth_last] A large U.S. construction firm had all of its current contract work and all previous project files crypto-locked by hackers who demanded $100K for their data. The breach encrypted $200M USD of future project data. Without proper remediation they may not have been in business today. [/three_fourth_last] [one_fourth] Texas Department of State Health Services [/one_fourth] [three_fourth_last] A recent attack at Texas DSHS resulted in the encryption of 10,000s of files at a regional hospital, affecting PCs and local file shares. [/three_fourth_last]
We are seeing incidents across all varieties of our customers and industries. Cybercriminals do not discriminate, but they do unfortunately prey on the weak – and the reality is that we’re seeing a higher proportion of attacks happening in organizations who do not have massive IT budgets with large security teams.
Quick pulse check: are you mad yet? Malware is not a new phenomena, but the explosive nature of this epidemic makes me mad as hell. It’s difficult enough for IT organizations to worry about losing data due to hardware failures and human error, now the fate of our companies – our jobs, our services, our progress and innovation – can literally hang in the balance of some lucky thug 5,000 miles away.
So – to borrow a phrase from a recent John Oliver segment on terrorism in Paris – f**k these cyber-criminals. At most, they are a seriously dangerous threat to an unprepared business. At least, they’re all capitalists who will only go after your data only so long as we are all prepared to pay to recover it. While it’s easy to pay for data recovery when you don’t have the right countermeasures in place and your back is to the wall, it’s equally easy to ignore ransomware attackers when your organization is prepared to deal with an attack.
Countermeasures to fight back against crypto-malware:
Step #1. Secure your perimeter to minimize the chance of breach:
- Patch your operating systems and keep your operating systems up to date. If you’ve not done that, stop reading and go do it right now. Seriously.
- Train employees on ransomware and their role in protecting the organization’s data.
- Disable macro scripts from office files transmitted over e-mail.
- Limit access to critical and rapidly-changing datasets to only need-to-know users.
That said, even the best firewall providers are challenged to keep pace with hackers.
Step #2. Back up all files and systems to avoid paying ransom to recover from crypto events.
- Backup your endpoints, back up your file servers.
- Implement lightweight, optimized data protection tools that minimize recovery points.
Back to our case studies, Texas Department of State Health Services is a great example of an organization with a comprehensive malware prevention and recovery agenda. While DSHS was using state-of-the-art firewall software to minimize the threat of malware breach, an unwitting user unfortunately downloaded a virus that was too new to be caught by DSHS’s enterprise virus scanning software. After 10,000s of files on a hospital’s file server were encrypted by ransomware, DSHS caught the issue and managed to roll back their files to a healthy state before their users even noticed. With a small data protection interval, they fortunately lost zero files in the process.
As much as I loathe the concept of capitalizing on misfortune, it is the case that CTERA and our customers have been fortunate to catch and recover from some very serious ransomware crypto-lock events. Using very granular file sync and backup procedures, CTERA customers have minimized their recovery points to as little as 5 minutes (versus 24 hours or more with competing technology). With the right data protection tools, they’ve successfully saved themselves from paying $100,000s in ransom and minimized the period of business outage
The only way we can put an end to this epidemic is by building the right safeguards that eliminate enterprise vulnerability and end the need to pay cyber-criminals to access our data and our systems. Whether you choose CTERA tools or any number of other approaches to safeguarding your organization, choose to be prepared and please do it right now.
Safe Keeping,
Jeff
Read Part Two of Jeff’s Ransomware Countermeasures post here.